Endpoint isolation is a technique used by cybersecurity solutions to segregate at-risk computers or other endpoint devices from the rest of the network in order to effectively remove the threat, run remediation and investigation processes and resolve security issues while mitigating lateral movement and any form of data exfiltration.
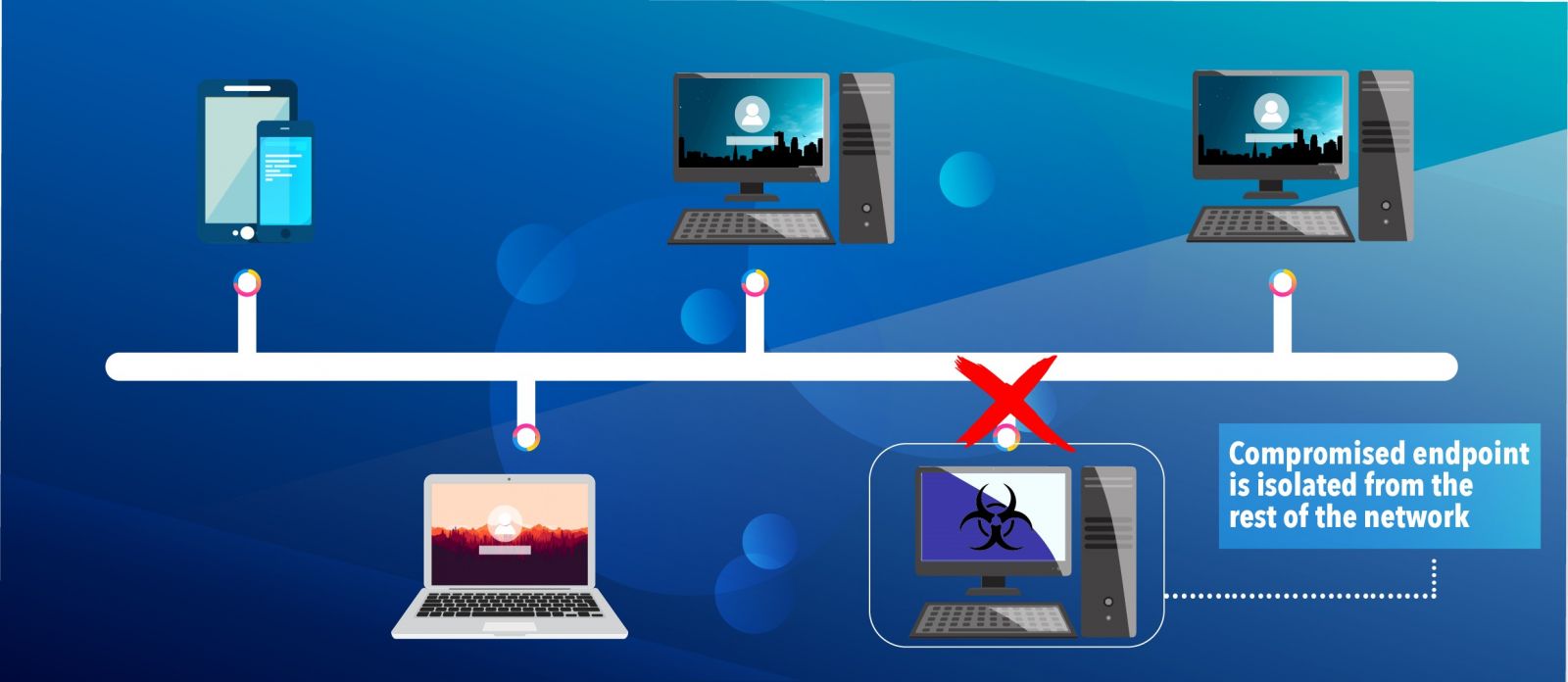
For example, when a breach occurs due to malware, the cybersecurity solution would pinpoint which endpoint has been compromised and isolate it to “stop the bleeding” and halt all network access on the endpoint.
By doing that, the malware won’t be able to phone home, which ensures that remote attackers are locked-out, and the compromised endpoint won’t be able to communicate with other endpoints in the network, which would greatly reduce or eliminate the attacker’s mobility.
Then, the security admin would be able to perform remediation tasks that include terminating processes, identifying, cleaning or removing infected files, restoring to the last good system configuration, or carrying out a detailed investigation of the breach.
There are different modes of endpoint isolation. Malwarebytes, for instance, leverages three modes of endpoint isolation in its own Endpoint Protection and Response solution. The three modes are:
Network Isolation – used to restrict which processes can communicate
Process Isolation – controls which processes are allowed to start, run and keep functioning on the endpoint
Desktop Isolation – alerts the end-user and immediately halts further interaction to limit the damage. The system is safely kept online, but it is only accessible via the Malwarebytes cloud console.
Having the different modes working in tandem ensures that the infection is kept under control and locked out before the remediation process is carried out.
